Dtex Systems.
We are the leading experts in next-generation insider threat protection.
Dtex is committed to helping enterprises run safer and smarter by providing an understanding of how their users interact with company data on their work devices. Hundreds of global enterprise customers use Dtex to detect credential misuse, stop data exfiltration and eliminate insider threats.

Agentless
Forwarder technology that records user telemetry (data) without impacting the performance of the endpoint.
Gold Award
Winner of the 2019 Cyber Security Excellence Gold award.
Cloud Service
Cloud based service that deploys across the enterprise within hours and delivers immediate value.
Product or Service Overview
Stop insider threats across your entire company, in the office or remote. Dtex’s next-gen insider threat platform allows companies of all sizes to operate securely and confidently, even with an increase in remote working.
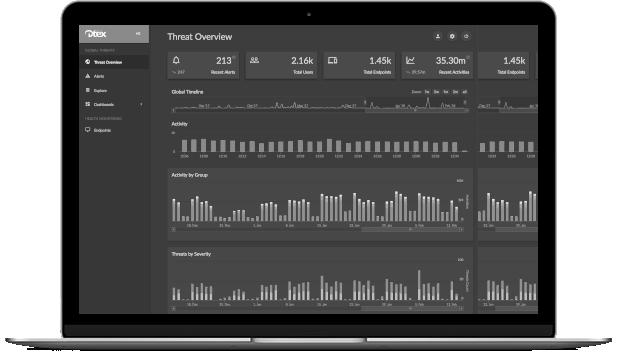
Dtex Intercept, collects and analyses user data from servers and workstations to identify inappropriate activity or behaviours indicative of a threat. This helps organisation retain their proprietary information and intellectual property, while maintaining regulatory compliance and their brand reputation.
Brand Protection
Protecting your organisation and brand reputation through the early identification of behaviours that lead to harmful data loss.
Behavioural Analysis
Detection of user behaviours that would breach compliance or lead to the loss of proprietary information.
Cost Recovery
Identifies application utilisation enabling organisations to recover the cost of unused licenses and remove unapproved applications.
Value
The overall value of the solution, focusing on effort, cost and optimal resource utilisation.
Benefit
The solution benefit, focusing on ease of integration, orchestration, automation and enhancing the performance of existing security technologies.
Outcome
The solution outcome in the reduction of risk, stakeholder confidence and maintained compliance.
- Reduced Effort 36%
- Reduced Cost 24%
- Optimal Resource 46%
- System Integration 24%
- Orchestration Automation 31%
- Enhancing Security 91%
- Risk Reduction 89%
- Stakeholder Confidence 82%
- Maintained Compliance 81%
Cloud based service or on-premises deployment, simply licensed by the number of endpoints protected.
Advanced ability to collect user telemetry (data) to identify inappropriate behaviours and activities that would lead to a breach of compliance or the loss or disclosure of proprietary information.